
AriaCloud is Docker container built for remote pentesting. From its Github home:
Aria Cloud is a Docker Container ideal for remote pentesting over SSH or RDP, with a primary emphasis on cloud security tools and secondary on Active Directory tools. Use it for an assumed breach pentest where remote access is necessary via RDP or SSH, or for simple AD lab testing. It is built for use cases where one needs to remote into a container using SSH or RDP, and then run their security workflows (i.e., Cloud environments). This repo also included an automated Terraform template + Ansible Playbook to deploy Aria Cloud as a container running on an Ubuntu Linux VM, with remote access over RDP.
In this post, I’ll quickly walk through what it is and show a demo. Full documentation can be found here.
Disclaimer: Please do not utilize anything you learn in this article for unauthorized or illegal purposes. Please ensure that you get permission from the network owner prior to running this tool against a network.
Use Cases
Beyond having a fun research tool to experiment with Docker networking, I wanted to put together an infrastructure pentesting tool for the following use cases:
- Cloud Penetration Testing Tools: A docker pentest container that has a lot of the cloud security pentest tools included. This makes the container very useful for cloud-focused security assessments. Feel free to fork it, clone it, and add whatever tools you want.
- Remote Pentesting with RDP and SSH Support: SSH or RDP into the container and run your tasks over an internal LAN. The project offers two separate images that are pre-built to use either SSH or RDP for remote access. The container exposes an SSH or RDP service over the host IP address and only requires a single docker run command. The RDP configuration uses XRDP and has been confirmed to work well with Microsoft RDP client and Rdesktop linux client.
- Assumed Breach Penetration Test: There is growing demand around “Assumed Breach Penetration Test” services or “Assumed Credential Leak” services. Especially in this COVID-19 pandemic, replacing an onsite consultant is essential. With this, the assessor might ship a laptop or a small form-factor box (i.e., Intel NUC, System76 Meerkat). The pentest box might establish a persistent auto-ssh reverse shell to the pentest infrastructure, avoiding inbound NAT or Firewall issues. Or they might just use the client’s VPN and remotely access a VM stood up for the pentest. This docker container can help meet those requirements but in a different way. The client simply installs Docker and you provide the container with some simple runtime instructions. You can then SSH or RDP into it and have access to the client’s network. You could even configure the container to run an auto SSH reverse SSH tunnel to your infrastructure, or (the easier option) use ngrok to expose an RDP/SSH tunnel behind a firewall. In comparison to shipping hardware or loading a Virtual Machine, a container is more lightweight, flexible, and portable.
- A Cloud Training Lab or Cyber Range: AriaCloud supports an automated deployment in Azure with Terraform templates. It also is included in an Active Directory Cyber Range. You can use it for training and attack simulations in your own cloud environment.
But how does this differ from the other docker containers and virtualization security tools already out there? I’m glad you asked because I always like to do some research on existing tools before deciding to build something new. First, the awesome folks over at Offensive Security have done and continue to do phenomenal things with Kali Linux. A huge shout out and tip of the hat to those guys. So this container is built on Kali Linux, of course 🙂 There is a Kali Linux VM offered in both Azure and Amazon marketplaces if that fits your needs.
AriaCloud supports RDP and it is a docker container. If you haven’t played with containers yet, they are very flexible, portable, and powerful. It includes all of the dependencies in the package and is easy and fast to share or customize. There are a couple of other community pentesting Docker containers. This one differs in that it packages a lot of cloud assessment tools, and it also supports remote RDP which slightly differs from the others. You can run it with a single command and don’t have to attach to the console first before starting a service that will enable remote access. The SSH or RDP service automatically starts and the XRDP configuration is already tuned and bundled with the container. Offering the Kali Linux Menu was a no-brainer and not just for people who prefer a GUI. The issue is there are some graph DB tools that I like such as Bloodhound that require Neo4J. The new RoadTools Azure assessment tool uses a web browser on localhost, so this feature is quite nice for other browser-based tools requiring a local UI on localhost.
Tools Included in Image
- Metapackages: kali-linux-core, kali-linux-top10, kali-desktop-core
- xRDP and SSH (for remote access)
- socat, powershell 7, smbclient
- AWS cli tools (aws, s3cmd)
- Azure cli tools (az)
- Google Cloud Platform cli tool (gcloud, kubectl)
- ROADTools (https://github.com/dirkjanm/ROADtools)
- Stormspotter (https://github.com/Azure/Stormspotter)
- ScoutSuite (https://github.com/nccgroup/ScoutSuite)
- Cloud_Enum (https://github.com/initstring/cloud_enum)
- cloudmapper (https://github.com/duo-labs/cloudmapper)
- Bucket Stream (https://github.com/eth0izzle/bucket-stream)
- Pacu (https://github.com/RhinoSecurityLabs/pacu)
- WeirdAAL (https://github.com/carnal0wnage/weirdAAL)
- evil-winrm (https://github.com/Hackplayers/evil-winrm)
- Impacket Python library and tools (https://github.com/SecureAuthCorp/impacket)
- Neo4j (https://neo4j.com/)
- Bloodhound (https://github.com/BloodHoundAD/BloodHound)
- Plumhound (https://github.com/DefensiveOrigins/PlumHound)
- Fox-IT Bloodhound-python data ingestor (https://github.com/fox-it/BloodHound.py)
- gitleaks (https://github.com/zricethezav/gitleaks)
- shhgit (https://github.com/eth0izzle/shhgit)
- gitrob (https://github.com/michenriksen/gitrob)
- Trufflehog (https://github.com/dxa4481/truffleHog)
- detect-secrets (https://github.com/Yelp/detect-secrets)
- Rubeus (https://github.com/GhostPack/Rubeus)
- Mimikatz (https://github.com/gentilkiwi/mimikatz)
Walk Through Demo of Building It with RDP Support
Now for the fun stuff. Let’s show a demo of deploying it with RDP support. In this example we’ll download it from my Docker Hub container registry and run it with the RDP use case. I’m currently running this test on an Ubuntu Linux 20.04 VM that has docker installed.
Step 1: Issue a docker pull to download it from the container repository:
docker pull iknowjason/aria-rdp:latest
It should look like this after the pull completion:

Step 2: Issue this command to run it. This will bind the RDP port and expose it on your host computer running Docker:
docker run -d --name myname2 -p 3389:3389 iknowjason/aria-rdp:latest
Step 3: Verify the listening port:
docker port myname2
The result should look like this:

Step 4: Grab your Docker host computer’s IP address that you will use for the RDP client. In my case, I’m running an Ubuntu VM with NAT and my Virtual Machine host is actually a Windows 10. I’ll just RDP to the Ubuntu VM guest’s NAT IP address.

Step 5: Use your RDP client to RDP into the container and let the Magic Happen. In this case I’m using mstsc as shown below:
Accept the default certificate with a yes.
The RDP prompt will look like this.

Username: aria
Password: !aria123!
After authenticating, you’ll see a couple of small errors ( On my To-Do list) but after that you’ll see a nice Kali Linux menu:

Most of the tools are installed into a standard /usr/local/bin PATH. For some of the special tools, they are installed into the /opt directory, as shown below:

Azure AD: ROADTools
Dirk-jan Mollema created an Azure AD pentesting framework and library called ROADTools. I’m very keen on this tool and Azure pentesting, so I’ll do a quick walk through of ROADTools using AriaCloud. The container bundles this very nice tool. Note that Azure pentesting tools are nascent and this particular tool is relatively new.
Step 1: Authenticate to the Azure tenant account with the correct options. For my lab, I have MFA enabled so I used the device-code authentication flow. This writes the authtoken to .roadtools_auth, as shown below. Follow the instructions and authenticate with your web browser.
roadrecon auth --device-code

Step 2: Run the roadtools gather command with roadrecon gather. This dumps all Azure objects that we will explore in a moment. If you used the device-code authentication, specify the file to use with — tokenfile.
roadrecon gather --tokenfile .roadtools_auth
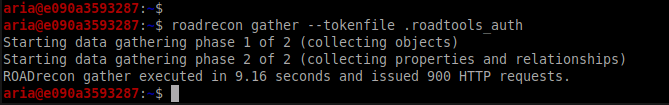
Step 3: Verify the roadrecon.db file that is created in the working directory.

Step 4: Launch the ROADRecon GUI and explore the data. Be sure to run the command specifying for it to open the roadrecon.db file created in Step 2.
roadrecon-gui --database roadrecon.db

Step 5: Launch Firefox browser and navigate to http://127.0.0.1:5000. Explore the data.

Next Steps
- Kubernetes tools
- Fix small RDP errors after initial authentication
- Fix Mac OS RDP client black screen (Microsoft Remote Desktop)
- Terraform templates for AWS deployment
Conclusion
Thank you for reading this and I hope you enjoy this tool as much as I enjoyed debugging and creating it. Containers are the future. The use cases for Cyber Security Containers will continue to grow. Fork it! Clone it! Let me know any ideas for future use cases.